5.5. Firewall
It’s a good idea to only open the ports you really need - especially for incoming traffic. In the most simple setup of one server containing all services you probably want 22 & 443 open for SSH & HTTPS and deny everything else. On Debian systems this can be accomplished using nftables.
This repository contains a simple nftables role for that. It is described in the roles chapter.
The firewall role is not meant to get very complex as firewall needs are very individual and on multiple layers anyway. If you want to extend its functionality for distributed servers you should probably move some differing variables from group_vars to host_vars. You can read more about host_vars here:
If GNU Health were distributed on multiple systems you would at least want to allow the following (assuming default ports):
- PostgreSQL:
Allow 5432 ingress, only coming from GNU Health
Allow 22 ingress, coming from Ansible controller
- GNU Health:
Allow 5432 egress, only to PostgreSQL
Allow 8443 (or 8000 or 3031) ingress, only coming from Nginx
Allow 22 ingress, coming from Ansible controller
- Nginx:
Allow 8443 (or 8000) egress, only to GNU Health
Allow 443 (& 80) ingress, only coming from your hospital (sub-)network
Allow 22 ingress, coming from Ansible controller
Note that the backup server with barman and restic already complicates the demand of ports as there are both SSH and PostgreSQL connections needed. The monitoring system and your own Certificate Authority (CA) could also be additional systems.
The visualization of Examples -> Production -> Extended shows the ports in use for this complex scenario:
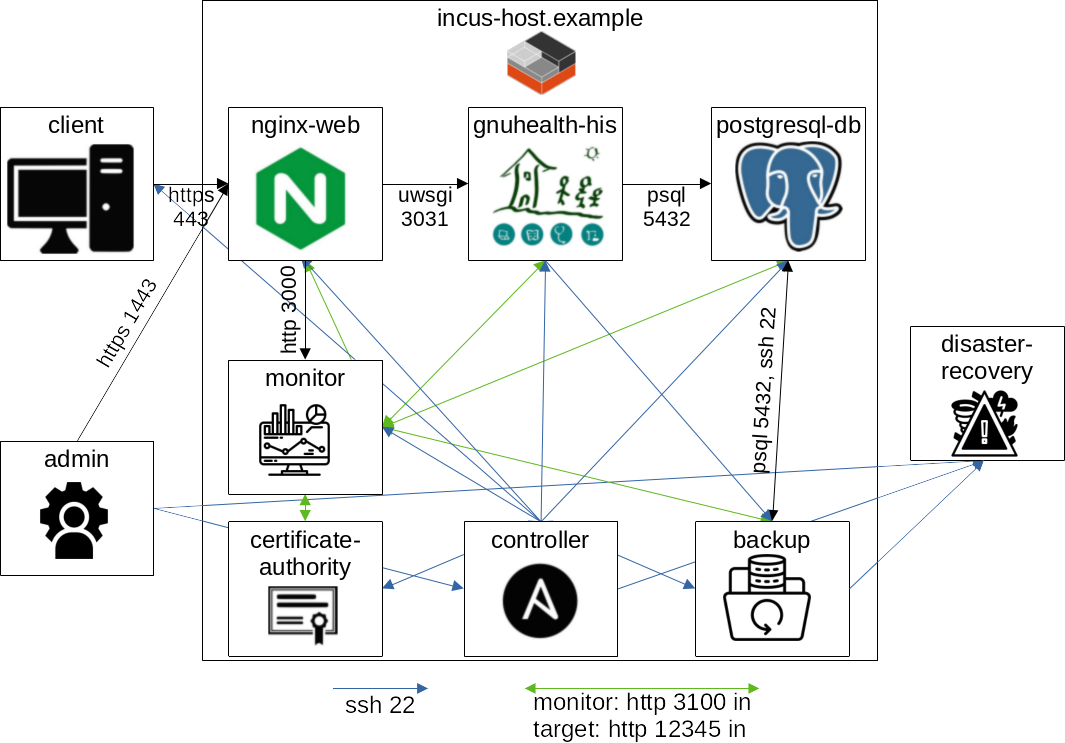
Ports needed for communication between the distinct systems. The directed arrows represent connection requests that still expect responses. All ports are only TCP. Arrows entering the Incus host imply an Incus proxy to forward the request. Icons that are not specific software logos taken from flaticon.com.
If you plan to restrict outgoing traffic you should also consider the one related to incoming traffic as responses, ports used by package installations, potential email notifications and any further functionalities you are using.